SOC 2 - Type 1 and 2
Cybersecurity is more critical than ever, with cyber incidents costing businesses worldwide billions each year. Data breaches, unauthorized access, and data misuse can devastate an organization’s reputation and finances, especially for service providers that handle client data. The AICPA’s SOC 2 (System and Organization Controls 2) compliance standard provides a framework to help service organizations demonstrate their commitment to security, availability, processing integrity, confidentiality, and privacy.
SOC 2 compliance enables companies to establish and maintain robust security controls tailored to today’s evolving cyber risks. By demonstrating adherence to SOC 2, your organization can showcase its dedication to protecting client data, which is an invaluable trust-building tool in competitive markets.
What is SOC 2?
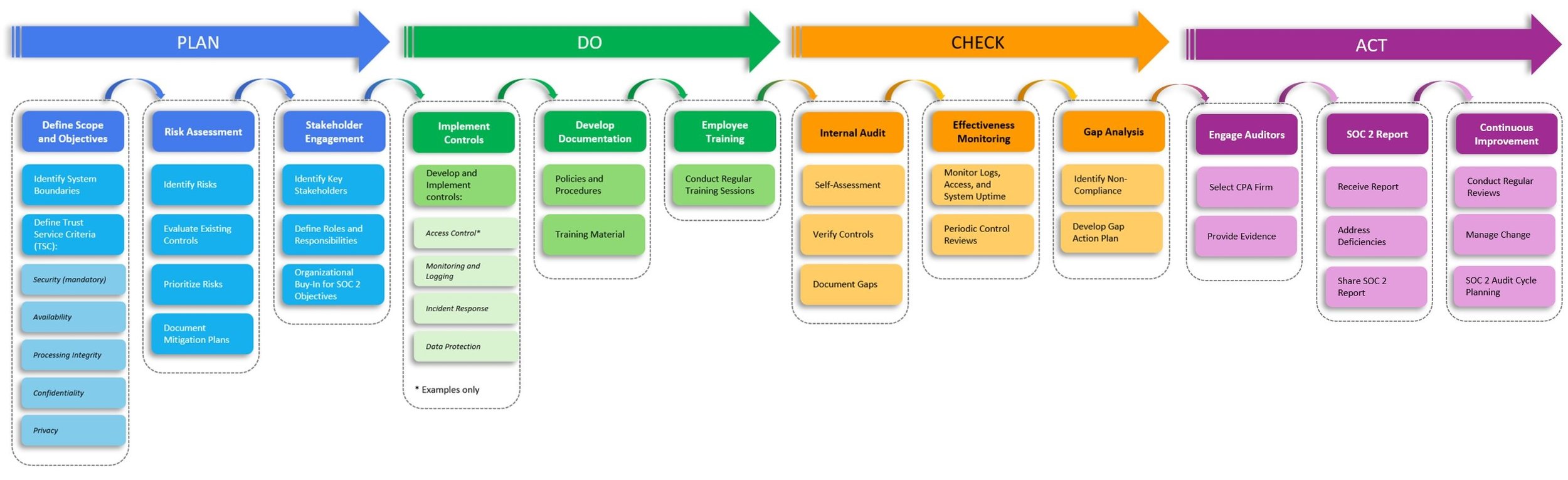
SOC 2 is a compliance framework developed by the American Institute of Certified Public Accountants (AICPA). It is specifically designed for technology and cloud computing organizations that handle client data, providing guidelines for managing data based on five critical Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
At its core, SOC 2 isn’t just about technical security controls; it also emphasizes operational processes, organizational culture, and proactive risk management. By integrating SOC 2 principles, companies can address information security holistically, which helps protect their organization and builds client confidence.
Is SOC 2 certification a good business decision?
Absolutely. SOC 2 compliance is increasingly recognized as a key differentiator, especially for service providers, SaaS companies, and cloud-based organizations. Compliance with SOC 2 helps businesses mitigate security and privacy risks, avoid costly fines, and meet contractual requirements, which boosts trust with existing clients and attracts new ones. SOC 2 reports provide verified evidence of your security controls, reassuring clients that your organization has established safeguards to protect their data and maintain a secure environment.
Why Cyber Compliance?
The CyberCompliance.io team brings over 20 years of experience in implementing information security frameworks, including SOC 2. Our experts understand the complexities of SOC 2 and have a proven track record in guiding organizations through its rigorous requirements. Our approach focuses on tailored solutions that meet your organization’s unique risk profile and compliance objectives.
One of the most frequently asked questions about SOC 2 compliance is, “How long does it take, and how much does it cost?”
CyberCompliance.io can answer that for you. Following an initial consultation where we assess your company’s specific needs, we’ll provide a free implementation timeline and cost estimate, helping you understand exactly what’s involved before making a commitment.
Why do we do this?
At CyberCompliance.io, our commitment is to exceed client expectations at every turn. We believe that understanding the investment required for SOC 2 compliance shouldn’t come with a price tag. We offer transparency and clarity because we know how valuable SOC 2 compliance can be for your business growth and client trust.
Contact us today for your free SOC 2 compliance timeline and cost estimate and take the first step toward building a secure and trusted business foundation. Let’s empower your organization with SOC 2 compliance and unlock the potential for stronger client relationships and business resilience.
Tools
Our approach to communication and collaboration.
Unlike many consulting firms that rely on rigid, in-house tools, we take a more flexible, client-centered approach. At CyberCompliance.io, we embrace the tools you're already comfortable with, ensuring a seamless integration where our team feels like a natural extension of yours. By working within your familiar systems, we enhance collaboration and efficiency every step of the way. Here are just some of the tools we utilize.
We utilize Slack Connect for all client communications to ensure you have immediate access to our Cyber Compliance team when you need us most, with real-time responses and continuous support right at your fingertips.
We utilize Asana to manage client projects, enabling them to collaborate, organize tasks, and track progress seamlessly. Its adaptability allows us to customize it easily to meet unique customer requirements.
We securely store all critical client documentation, policies, and procedures in Google Drive, ensuring seamless sharing and version control. Strict access management is enforced to protect sensitive information and maintain confidentiality.
We use Fathom.ai to transcribe meetings, ensuring every conversation is captured in detail. This allows participants to stay fully focused on the discussion, avoiding distractions from note-taking and providing accurate records for review.