ISO/IEC 27001:2022 Information Security Management System (ISMS)
A cyberattack occurs every 39 seconds, and there has been a staggering 300% increase in cyber threats since 2019. Businesses of all sizes face constant and widespread cyber threats, which cause significant financial losses and impact operational efficiency and brand reputation. Cisco defines cybersecurity as "the practice of protecting systems, networks, and programs from digital attacks." This discipline involves actively preventing, monitoring, and resolving cyber threats by implementing safeguards (controls) designed to mitigate security risks.
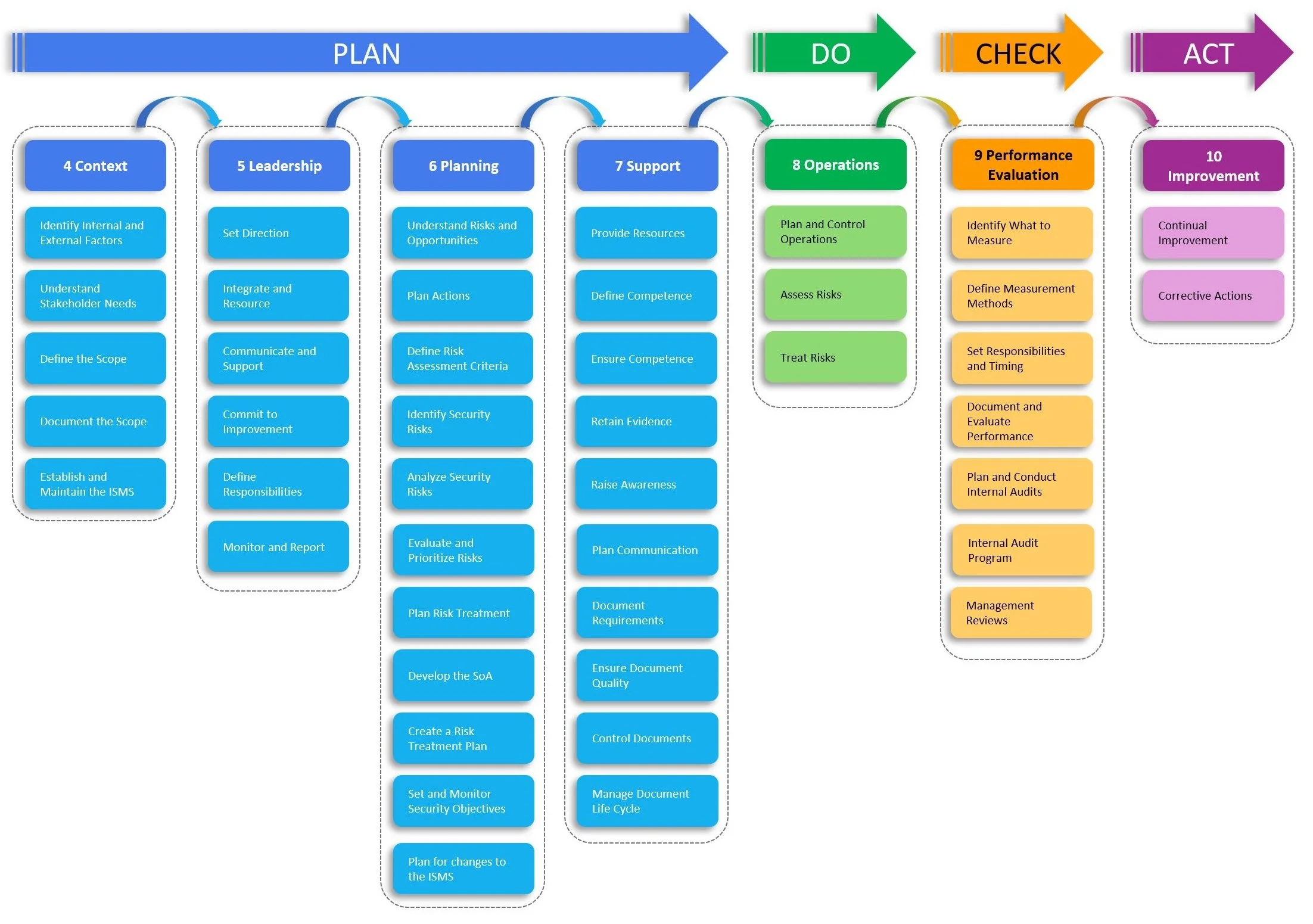
ISO/IEC 27001:2022 (ISO 27001) is a risk-based standard that helps organizations manage the security of their information by identifying and mitigating security risks. It provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System.
What is an Information Security Management System (ISMS)?
An Information Security Management System (ISMS) is a comprehensive approach to managing an organization's most valuable asset: data. It involves implementing and maintaining a set of policies, procedures, and guidelines designed to prevent unauthorized access to data (confidentiality), protect data from unauthorized modification or destruction (integrity), and allow authorized users to access systems, networks, and applications when they are needed (availability).
At its core, an ISMS is a systematic and proactive approach to managing data. It helps businesses identify, assess, and prioritize their information security risks and implement controls to mitigate those risks. It's not just about prevention but also about continuous improvement, as it includes ongoing monitoring and review processes to ensure the effectiveness of the safeguards (controls) and to identify and address any weaknesses.
Is ISO/IEC 27001:2022 certification a good business decision?
The simple answer is yes, it really is. ISO/IEC 27001:2022 certification is a valuable asset for businesses, regardless of industry or size. It demonstrates to customers that the company is dedicated to safeguarding their data and fulfilling contractual security requirements. An ISO/IEC 27001:2022 ISMS can also assist businesses in meeting industry-specific compliance requirements, avoiding penalties, and building trust with customers and business partners.
Why Cyber Compliance?
The CyberCompliance.io team has over 20 years of experience in implementing an ISO/IEC 27001:2022 ISMS. They excel at developing and implementing robust security solutions tailored to diverse organizational needs and crafting comprehensive information security policies, procedures, and risk assessments aligned with industry best practices.
A question that’s always asked when implementing an ISO/IEC 27001:2022 ISMS is, “How long does it take, and how much does it cost?”
CyberCompliance.io can answer this for you. After an initial consultation, during which we gather an overview of your company and ISMS requirements, we’ll provide you with a free ISMS implementation timeframe and cost estimate!
Why do we do this? CyberCompliance.io is dedicated to exceeding our customers' expectations in every way. We appreciate that implementing an ISO/IEC 27001:2022 ISMS has a cost, but we don’t think you should have to pay to understand what that cost might look like.
Contact us today for your free ISMS implementation timeframe and cost estimate, and begin the journey of empowering your organization's information security and risk management with an ISO/IEC 27001:2022-compliant ISMS.
Tools
Our approach to communication and collaboration.
Unlike many consulting firms that rely on rigid, in-house tools, we take a more flexible, client-centered approach. At CyberCompliance.io, we embrace the tools you're already comfortable with, ensuring a seamless integration where our team feels like a natural extension of yours. By working within your familiar systems, we enhance collaboration and efficiency every step of the way. Here are just some of the tools we utilize.
We utilize Slack Connect for all client communications to ensure you have immediate access to our Cyber Compliance team when you need us most, with real-time responses and continuous support right at your fingertips.
We utilize Asana to manage client projects, enabling them to collaborate, organize tasks, and track progress seamlessly. Its adaptability allows us to customize it easily to meet unique customer requirements.
We securely store all critical client documentation, policies, and procedures in Google Drive, ensuring seamless sharing and version control. Strict access management is enforced to protect sensitive information and maintain confidentiality.
We use Fathom.ai to transcribe meetings, ensuring every conversation is captured in detail. This allows participants to stay fully focused on the discussion, avoiding distractions from note-taking and providing accurate records for review.